DVWA - Configure Burp
We will use Burp Suite to solve the DVWA challenges. To do so we need to configure the tool and our web browser.
Burp Suite installation
Please refer to the official documentation to learn how to install Burp.
On Linux you just have to download and run a script.
Starting Burp Suite
Once Burp Suite is installed start it. The Community Edition of Burp Suite only allows for temporary projects, so choose this and click next.
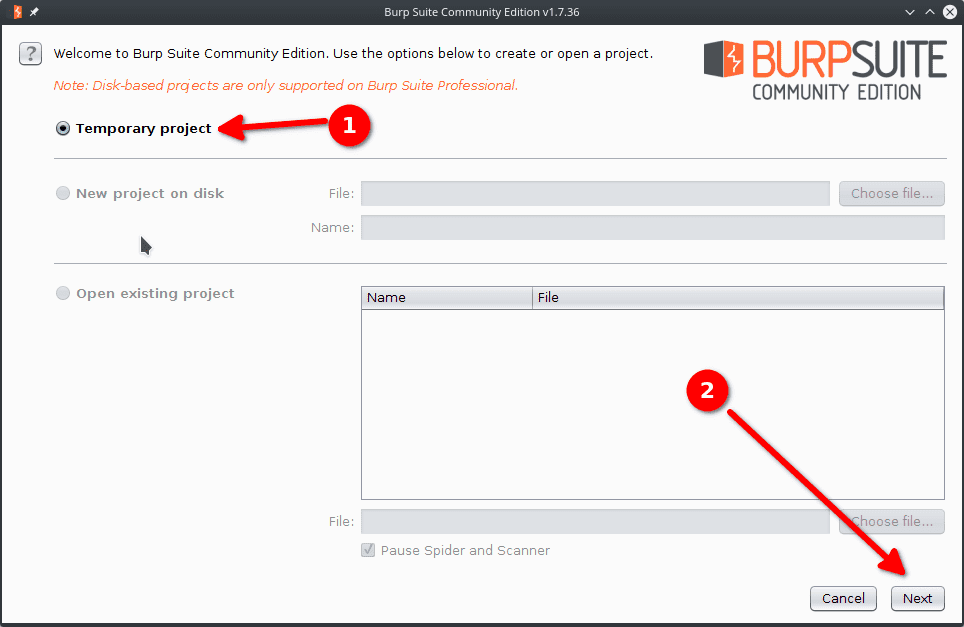
Since we haven't got a configuration yet we choose Burp defaults on the next screen. Later on we can save our config in a file a reload it on the next Burp launch.
Configuring the target scope
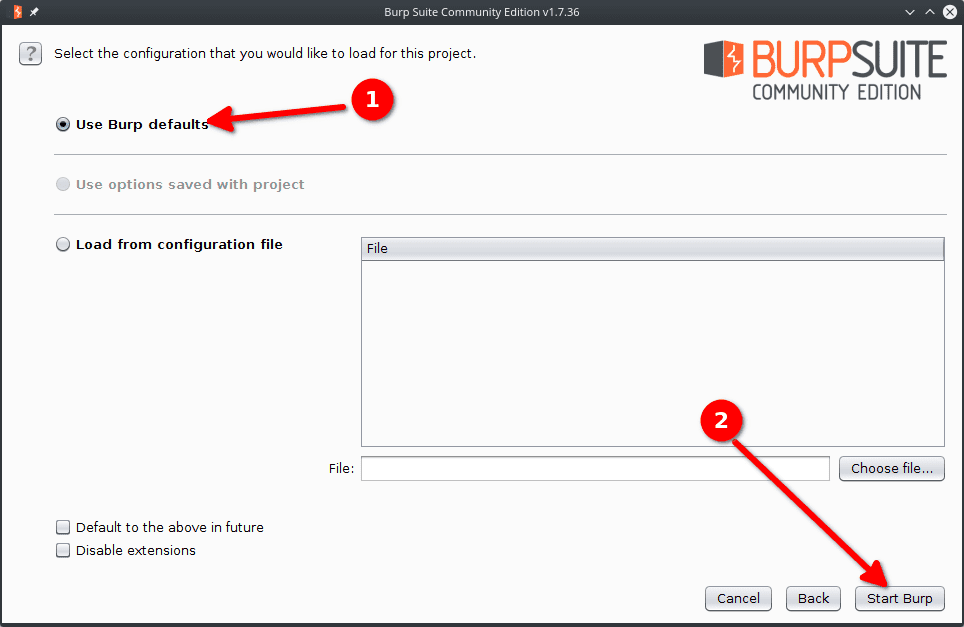
Burp Suite is now started. The first thing to do is to configure our target scope which will define the requests we will intercept and modify. To do so :
- Target > Scope > Add.
- Set the prefix to
localhost. - Click OK.
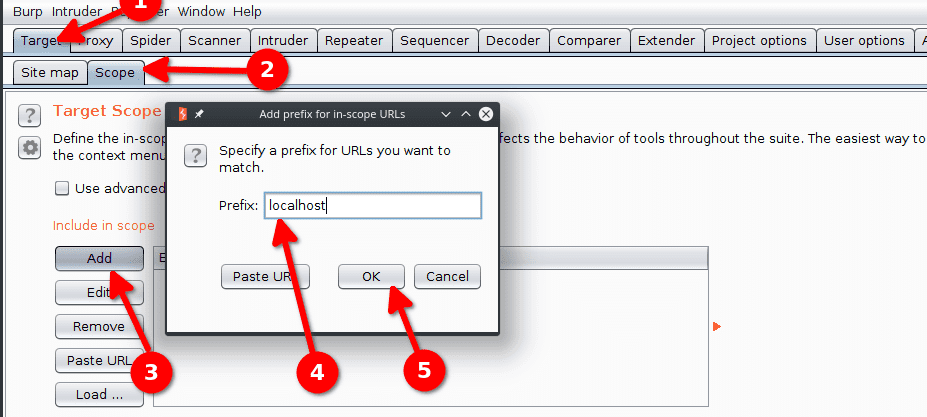
We choose to avoid accumulating data and click Yes on the pop up that follows.
Configuring the interception options
We configure the proxy to intercept the client requests and server responses only when the URL is in the target scope.
To do so :
- Proxy > Options > Intercept Client Requests.
- Check the box
And URL Is in target scope.
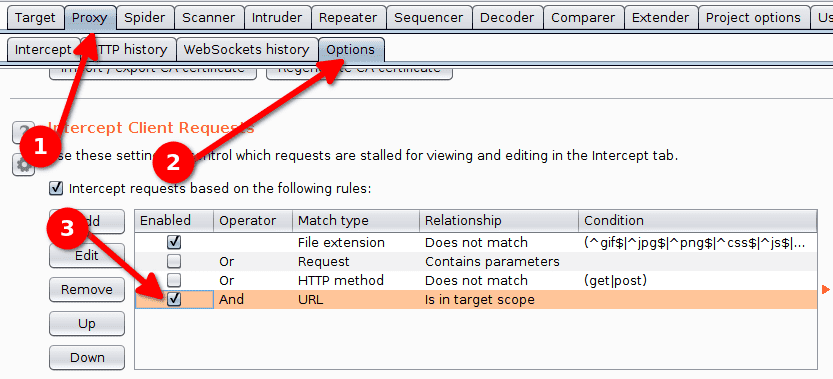
Do the same for the option Intercept Server Responses.
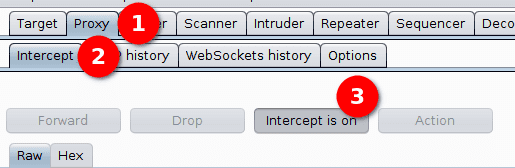
We now disable the interception, we will enable it when needed. To do so Proxy > Intercept > Intercept is on.
Configure your browser proxy
Burp suite proxy is by default 127.0.0.1:8080.
We configure our Firefox proxy to redirect all requests to Burp.
To do so :
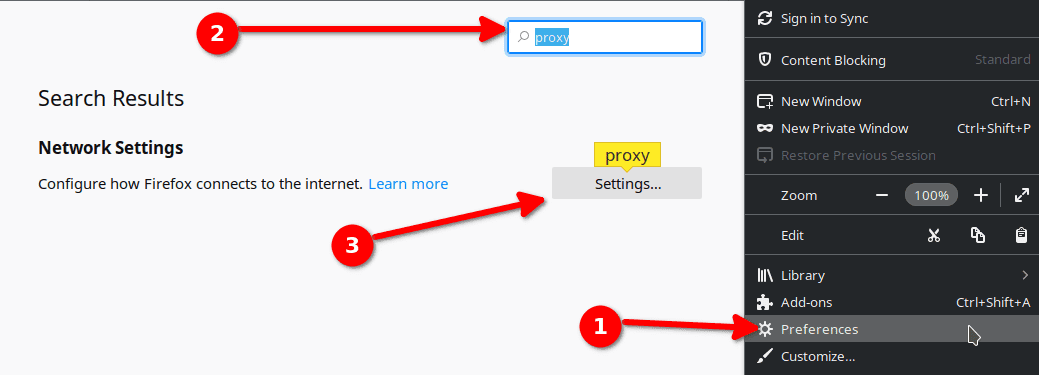
- Click Preferences in the Firefox menu.
- Search for proxy.
- Click on Settings....
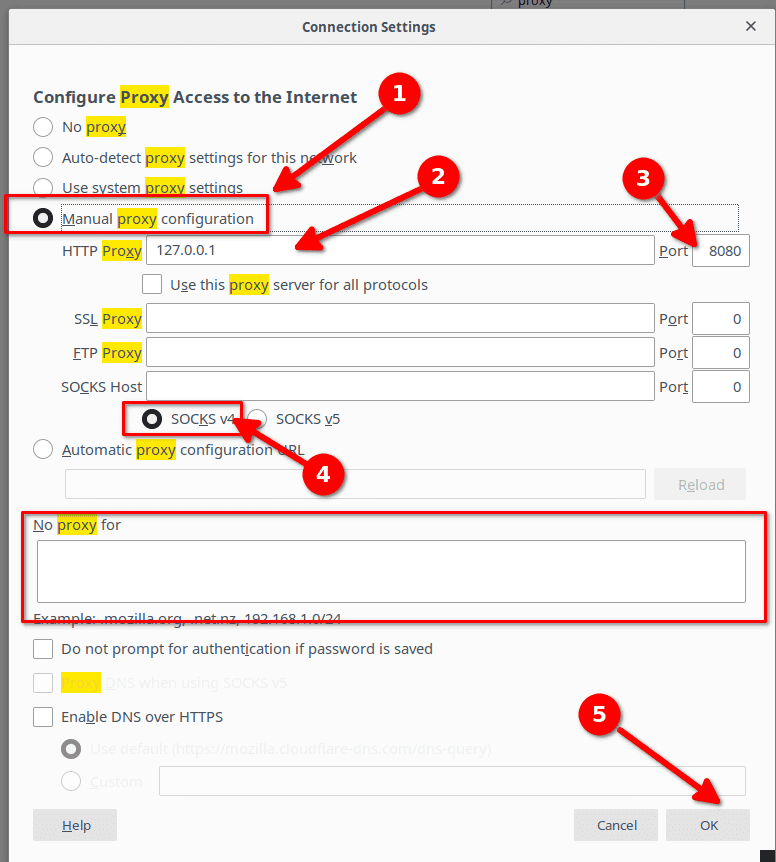
Then configure the proxy with the following settings.
| Setting | Value |
|---|---|
| Manual proxy configuration | Checked |
| HTTP Proxy | 127.0.0.1 |
| Port | 8080 |
| SOCKS v4 | Checked |
| No Proxy for | Empty |
Firefox is now setup to use Burp as its proxy. You can now do some challenges with Burp Suite and Firefox.